Your Single Source of Compliance Truth
Access curated regulatory content, security vulnerability data (CVE, CWE, CAPEC), and your own project documents, all in one searchable library.
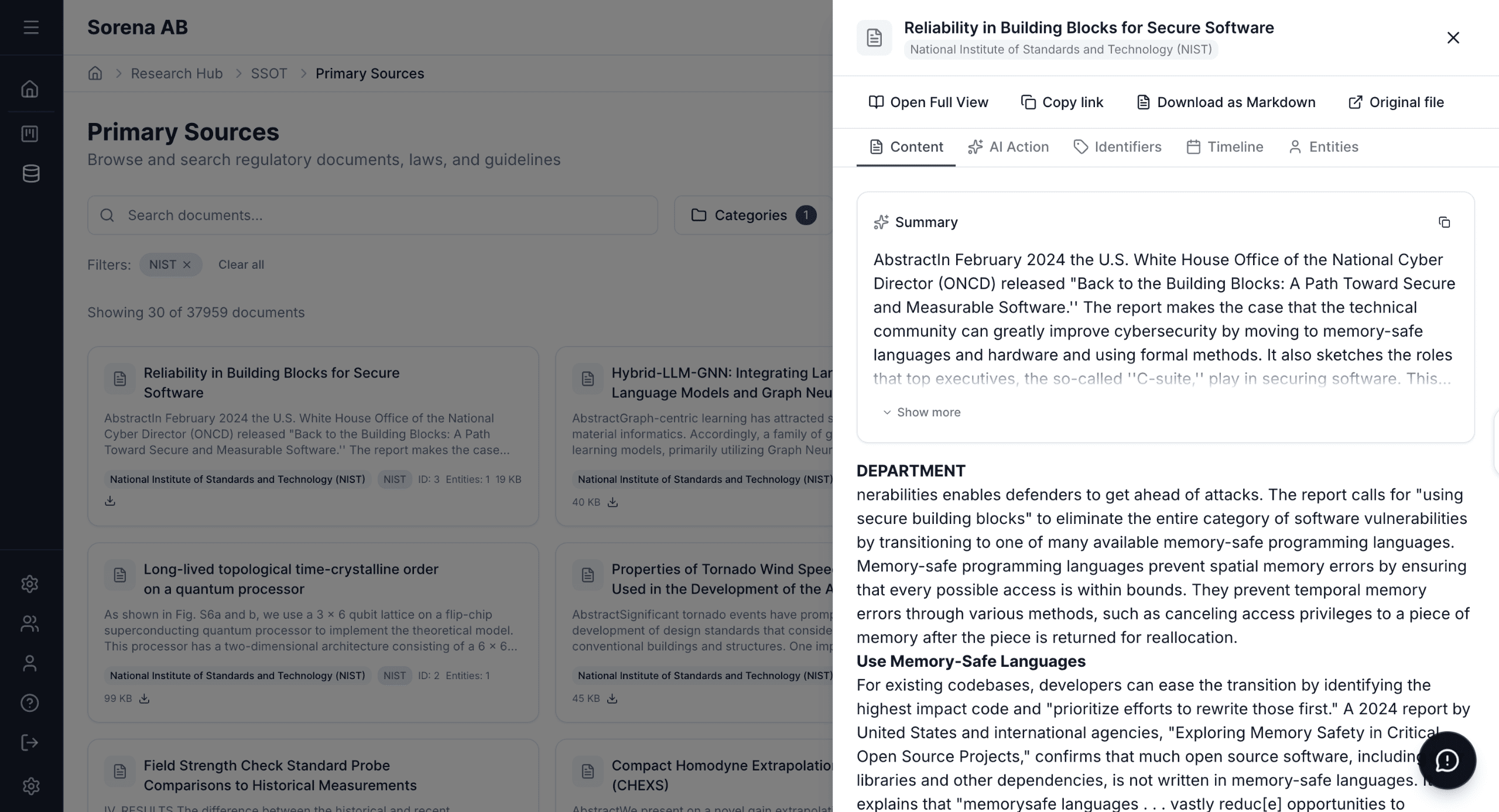
From Scattered to Searchable
SSOT puts authoritative regulatory content and security data at your fingertips.
Browse Library
Explore curated regulatory content organized by category: Swedish laws, NIST frameworks, ETSI standards, and EU regulations.
Search & Filter
Use powerful filters to narrow down by category, source, or security classification. Search with debounced queries for fast results.
Preview Documents
View document details in the side drawer without leaving the search view. See metadata, summaries, and quick actions.
Upload to Projects
Add your own documents to project workspaces. Uploaded files become searchable by the Research Copilot.
Built for Compliance Document Management
Curated Primary Sources
Access a comprehensive library of regulatory content including Swedish laws, NIST frameworks, ETSI standards, and European Union regulations.
Security Vulnerability Data
Includes CVE, CWE, and CAPEC datasets for vulnerability research. Filter by severity, category, or attack pattern to inform your security assessments.
Category Navigation
Browse documents through an intuitive category tree. Filter by source, security classification, or document type to find what you need.
Project Integration
Upload your own documents to project workspaces. Project files are indexed and searchable by the Research Copilot for contextual answers.
Organize Everything in One Place
Policies & Procedures
- Information Security Policy
- Incident Response Plan
- Access Control Procedures
Regulatory Guidance
- GDPR Guidelines
- SOX Requirements
- Industry Circulars
Standards & Frameworks
- ISO 27001
- NIST CSF
- SOC 2 Criteria
Security Datasets
- CVE Vulnerabilities
- CWE Weaknesses
- CAPEC Attack Patterns
The Cost of Scattered Information
Workers struggle with too much time spent searching for information
Time spent communicating rather than creating value
Average number of apps used at an organization
Annual cost of poor data quality in the U.S.
Built for Your Industry
Financial Services
Aggregate regulatory guidance, market data, and customer KYC/communications with retention and auditability. Recordkeeping failures have driven large fines, e.g., $289M across 11 firms.
Healthcare
Integrate EHR documents, medical literature, and safety alerts with proper provenance and permissions while improving recall and decision-making speed.
Technology
Connect documentation, repositories, issues, and runbooks to speed troubleshooting with semantic retrieval and cross-system intelligence.
Legal Services
Integrated legal research, client files, and regulatory updates with unified search across verified sources, reducing time-to-answer significantly.
Common Questions
What content is in the library?
SSOT includes curated regulatory content (Swedish laws, NIST frameworks, ETSI standards, EU regulations), security vulnerability datasets (CVE, CWE, CAPEC), and your own project documents.
What security data is included?
SSOT includes CVE (Common Vulnerabilities and Exposures), CWE (Common Weakness Enumeration), and CAPEC (Common Attack Pattern Enumeration and Classification) datasets for vulnerability research and threat modeling.
How does search work?
Use the search bar with debounced queries for fast results. Filter by categories, sources, severity levels, or security classification using filter chips. Toggle between grid and list views.
Can I add my own documents?
Yes. Upload documents to your project workspaces through the Storage Browser. Uploaded files are indexed and become searchable by the Research Copilot for project-specific context.
Ready for a Single Source of Truth?
See how SSOT can centralize your regulatory content, security data, and project documents.
Explore other solutions